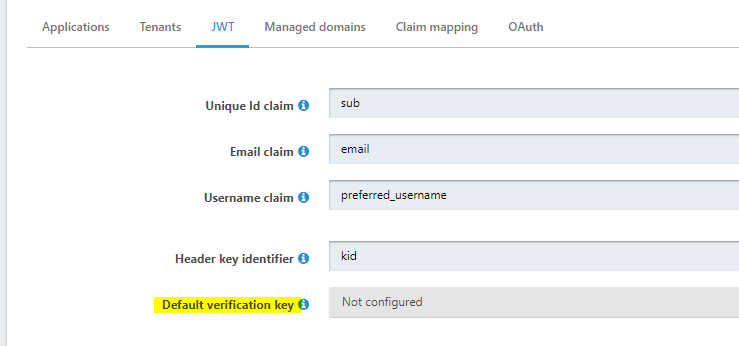
@dan thanks for your answer.
I believe it should be possible to add this restriction in FusionAuth by configuration, as it presents a security issue for integrations using more than one External JWT. And as FusionAuth is multi-tenant, this could seriously go wrong.
What I would like to propose, is that the setting Default verification key is changed into Verification key. If the token contains a kid, it must match with what is configured there and the signature must be correct. If the token does not contain a kid, the signature must be correct according to the key selected there. Is this the correct place to request such feature?