Can't use api login with azure ad
-
Hi,
We are switching from crowd to fusionauth. One of the requirements is to use FusionAuth as proxy authentication provider for Azure AD. So far we've have configured OpenID Connect to use Azure AD of our company. Via the hosted login pages of fusionauth we're abled to login. But we need the api to login and this is not working. We have our own login services etc in place.
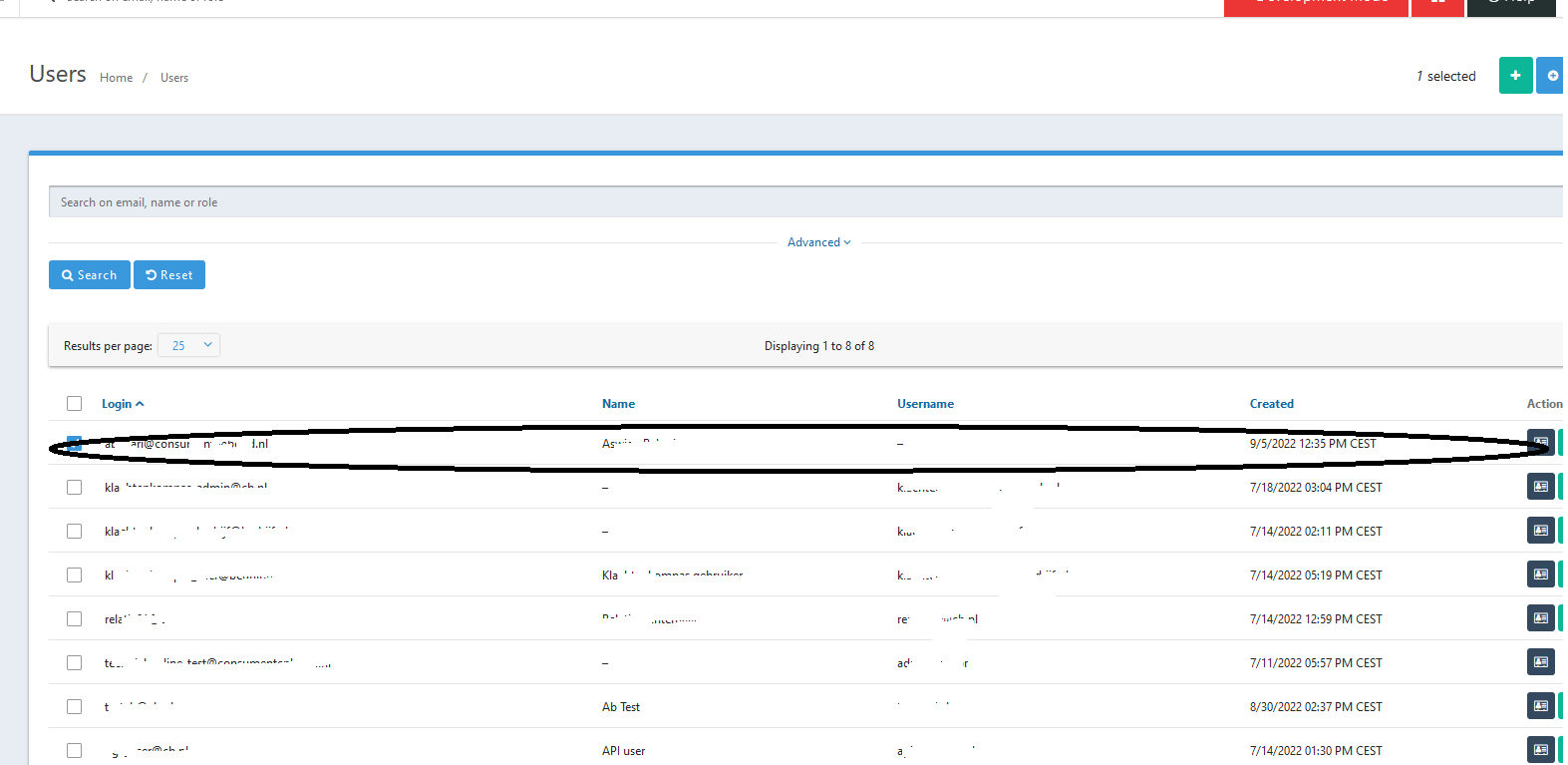
When we login via de hosted login page the login is successful and a linked user is created.
User created when logged in via the hosted page
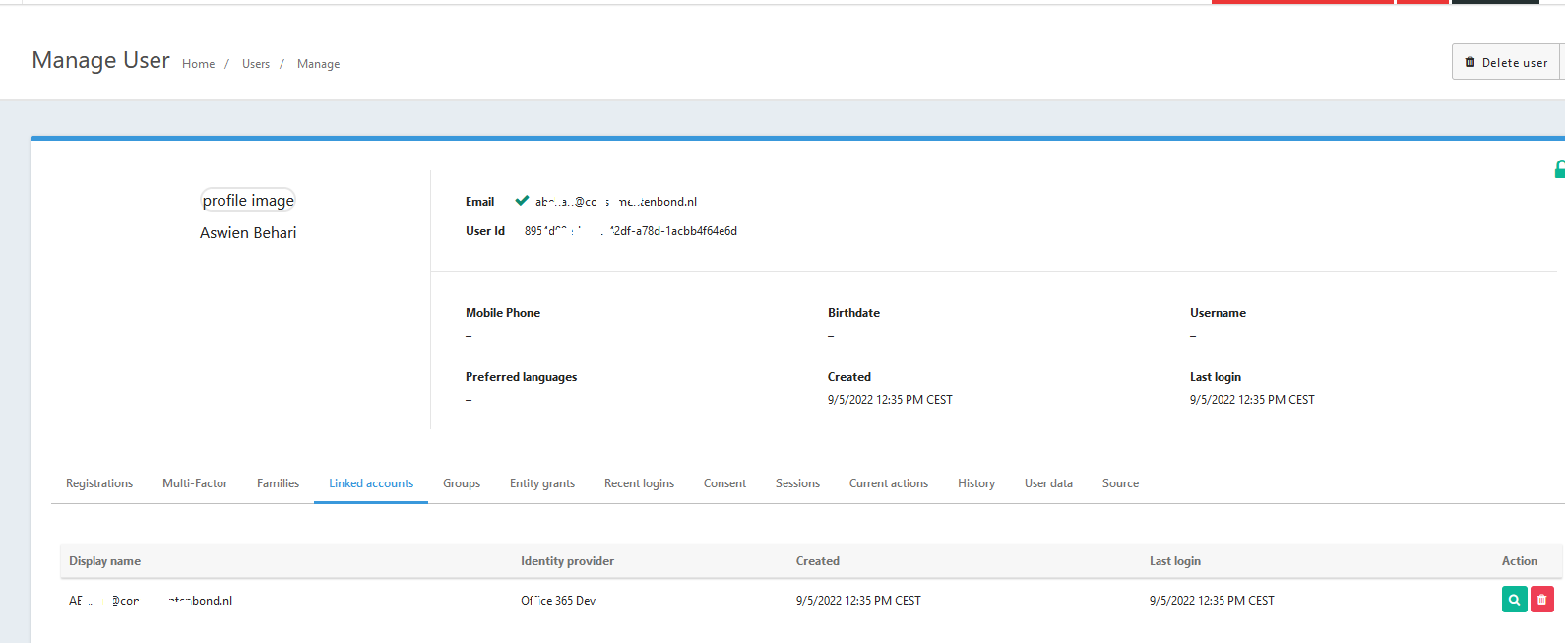
OpenID connect config
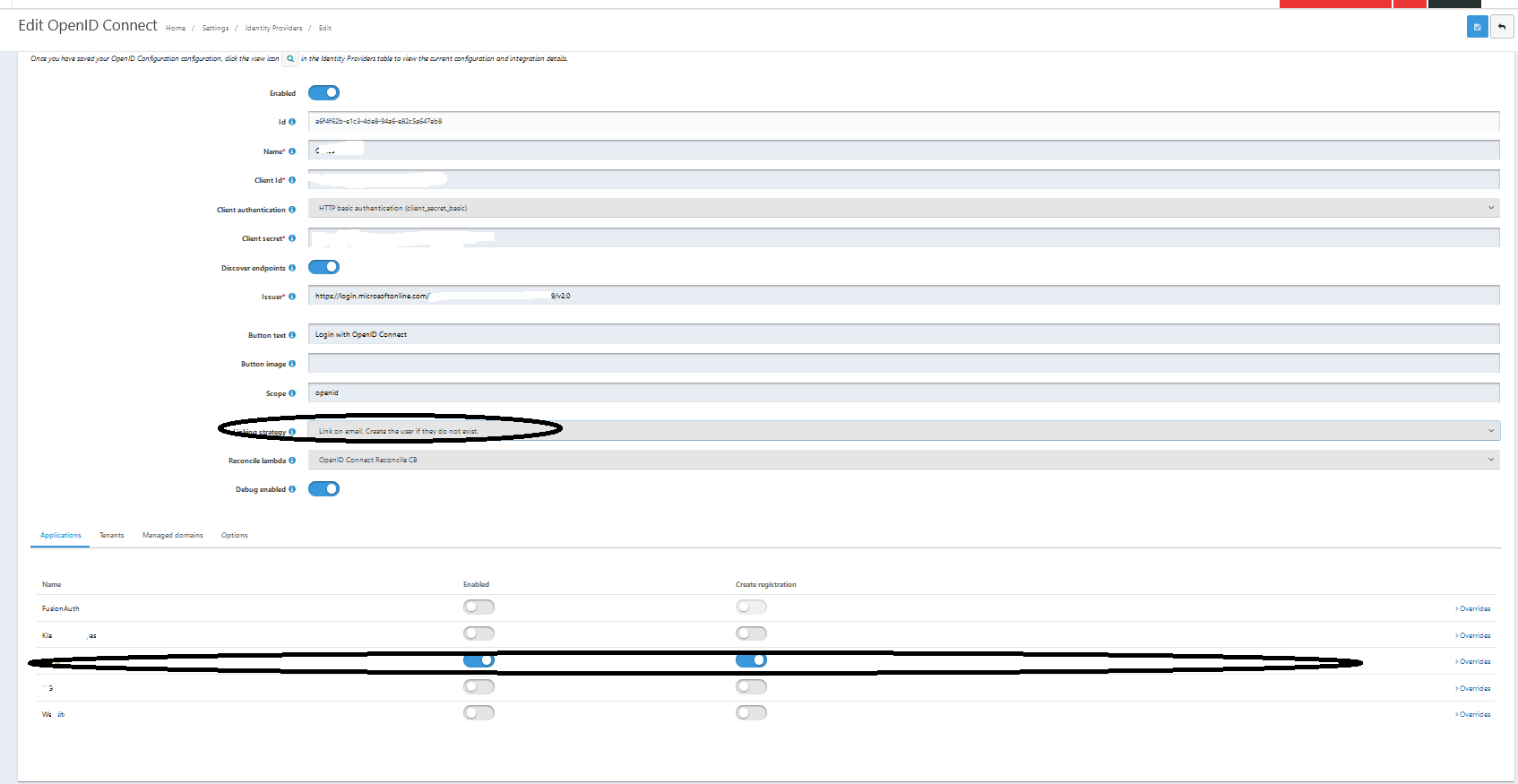
When trying to login in via the api, it returns 404. The user is not found.
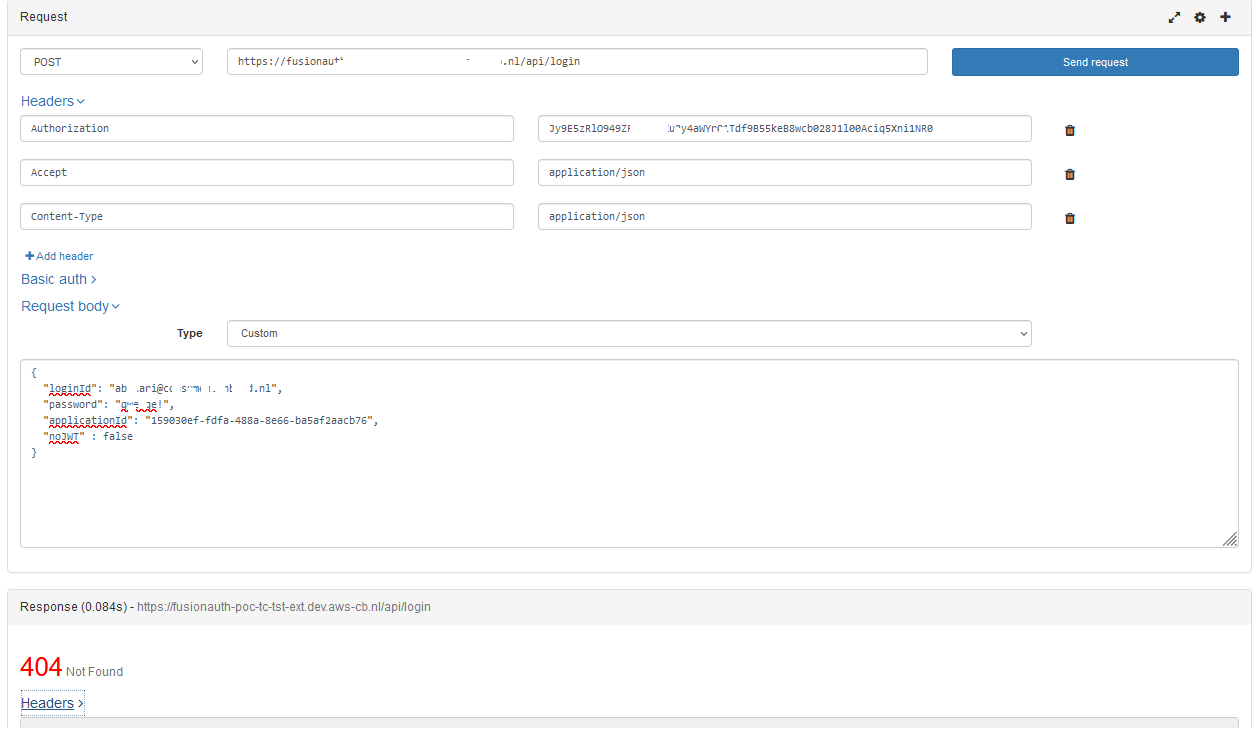
When change the usre to have a password in fusionAuth, the the user is return via the api. That's is not what we want. We want to manage the password in azure and use fusionauth only as a login proxy with our own custom login in out back end application.
What are we doing wrong?
Regards,
Aswien -
@abehari Thanks for the question -
The user is not found when they are initially linked as they are tied to an external auth store (azure in this case), so we are relying on Azure to store the user's password/credentials (federation). Once you create a user with a password, and call the
api/loginwe are going to look in our database and if the user is found (and with the correct credentials), we will return (as you experienced).I am wondering if using the login API for OIDC provider is more appropriate for your use case
In this case, you are building your own login pages, in which you call Azure, and on that final step, called
complete the login, you are asking FusionAuth to log the user in based on what Azure says.Let us know if that better addresses your use case.
Thanks,
Josh -
Hi @joshua thanks for your reply. We've tried the suggested "Complete an OpenID Connect Login", but the problem is we don't understand where to get de "code" from. And we don't have any redirect uri (callback url) in our application. Where and when should the 'code" be returned and by whom?
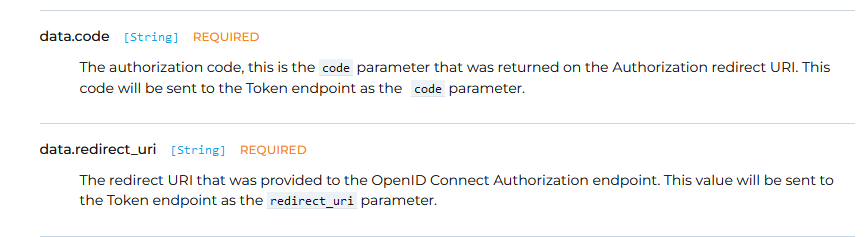
In our application we're doing a rest (json based) login via a java rest client and we like to maintain that. We have no login pages etc. You can login with postman. Is that possible with fusionauth?
Postman (Request) -> Our application (Rest) ->FusionAuth -> Azure AD -> FusionAuth (some token) -> Our application (Rest, we generate our own JWT, based on fusionAuth token and additional information) -> Postman (JWT response). Is this possible?
Regards,
Aswien -
 J joshua has marked this topic as solved on
J joshua has marked this topic as solved on
-
Marking this as "solved" as this was addressed out of band. Let us know if there are any other questions.
Thanks,
Josh